Security & Defence
Military, police, intelligence, and civil protection organisations.
Military, police, intelligence, and civil protection organizations requiring high-assurance, sovereign solutions for sensitive operations.
Exercise Total Defence 2026 (TFX26)
National total defence exercise focusing on civil-military cooperation, critical societal functions, and digital crisis management. Norway's largest exercise since the Cold War.
Defence Conference 2026
Conference on defence, technology, and security, including digitalization and the cyber domain.
CyCon 2026
NATO CCDCOE's premier multidisciplinary conference examining technical, legal, policy, strategic, and military dimensions of cyber defence. Brings together global experts on cyber conflict and security.
Total Defence Cybersecurity Conference 2026
Conference focused on cybersecurity, digital sovereignty, and total defence. Arena for exploring how totalforsvaret can be strengthened through open dialogue, expert deep-dives, and political perspectives.
BEFKON - Defence and Preparedness Conference Innlandet 2026
Regional conference gathering preparedness actors, Armed Forces, industry, and political leadership from Innlandet to discuss total defence status and challenges during the Total Defence Year 2026.
Total Defence Conference 2026
Annual conference on total defence with civil-military cooperation, including critical infrastructure, IT, and digital resilience.
Civil Security Conference 2026
National conference on civil security, total defence, and digital preparedness, including cybersecurity and information security.
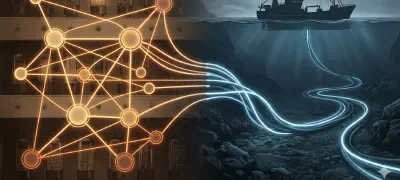
From ARPANET to Amazon: How We Broke the Internet's Original Promise
The internet was built to survive nuclear war. We've since made it vulnerable to fishing trawlers and policy changes in Washington. The same architecture designed for resilience has been recentralized - and Russia is already testing our cables.

The Hybrid War Is Already Here: Why Digital Sovereignty Can't Wait
GPS jamming 294 days a year. A Norwegian dam hacked by pro-Russian actors. 40 sabotage operations across Europe. The hybrid war isn't coming - it's happening now. And our digital infrastructure is dangerously exposed.

Totalberedskapsmeldingen 2025
Norwegian Government's comprehensive national preparedness strategy covering civil-military cooperation, digital resilience, and societal security

Humanitarian Security in an Age of Uncertainty: The Intersection of Digital and Physical Risks
Practitioner guidance on integrating digital threats into security risk management

FFI: Frivillige beredskapsorganisasjoner i totalforsvaret
Norwegian Defence Research Establishment analysis of voluntary preparedness organizations' role in total defence

Safeguarding Humanitarian Organisations from Digital Threats
ICRC analysis of how cyber operations, data breaches, and disinformation cause real-world harm to humanitarian organisations
CLOUD Act
US law enabling law enforcement to compel US technology companies to disclose data regardless of where it is physically stored.
DORA
EU regulation establishing ICT risk management and digital resilience requirements for the financial sector.
ECPA
US law governing government access to electronic communications, with different standards for content, metadata, and stored communications.
Ekomloven
Norwegian law regulating electronic communications networks, services, and lawful interception requirements.
EO 12333
Presidential directive authorizing US intelligence agencies to collect signals intelligence on foreign targets outside US territory.
FISA Section 702
US law authorizing warrantless surveillance of non-US persons located outside the United States for foreign intelligence purposes.
Investigatory Powers Act
UK law granting intelligence and law enforcement agencies broad surveillance powers including bulk data collection and equipment interference.
IT Act
Indian law enabling government interception, monitoring, and decryption of any computer resource in the interest of national security.
LED
EU directive setting data protection rules for police and criminal justice authorities.
National Intelligence Law
Chinese law requiring all organizations and citizens to support, assist, and cooperate with state intelligence activities.
National Security Act
UK law creating new criminal offenses for espionage, foreign interference, and sabotage, with powers to address state threats.
NIS2 Directive
EU directive mandating cybersecurity requirements for essential and important entities across critical sectors.
Patriot Act
Post-9/11 US law significantly expanding surveillance powers for terrorism investigations, including Section 215 business records collection.
Sikkerhetsloven
Norwegian law protecting national security through security clearances, classified information protection, and critical infrastructure safeguards.
SORM
Russian system requiring all telecommunications providers to install FSB-accessible surveillance backdoors.
TOLA Act
Australian law enabling authorities to compel technology companies to build backdoors, assist with decryption, and provide technical capabilities for surveillance.
Yarovaya Law
Russian anti-terrorism law requiring communications data retention for 6 months and mandatory assistance with decryption.